Most Recent Arcitura Education S90.20 Exam Dumps
Prepare for the Arcitura Education SOA Security Lab exam with our extensive collection of questions and answers. These practice Q&A are updated according to the latest syllabus, providing you with the tools needed to review and test your knowledge.
QA4Exam focus on the latest syllabus and exam objectives, our practice Q&A are designed to help you identify key topics and solidify your understanding. By focusing on the core curriculum, These Questions & Answers helps you cover all the essential topics, ensuring you're well-prepared for every section of the exam. Each question comes with a detailed explanation, offering valuable insights and helping you to learn from your mistakes. Whether you're looking to assess your progress or dive deeper into complex topics, our updated Q&A will provide the support you need to confidently approach the Arcitura Education S90.20 exam and achieve success.
The questions for S90.20 were last updated on Feb 18, 2025.
- Viewing page 1 out of 6 pages.
- Viewing questions 1-5 out of 30 questions
Service A provides a customized report generating capability. Due to infrastructure limitations, the number of service consumers permitted to access Service A concurrently is strictly controlled. Service A validates request messages based on the supplied credentials (1). If the authentication of the request message is successful, Service A sends a message to Service B (2) to retrieve the required data from Database A (3). Service A stores the response from Service B (4) in memory and then issues a request message to Service C (5). Service C retrieves a different set of data from Database A (6) and sends the result back to Service A (7). Service A consolidates the data received from Services B and C and sends the generated report in the response message to its service consumer (8).
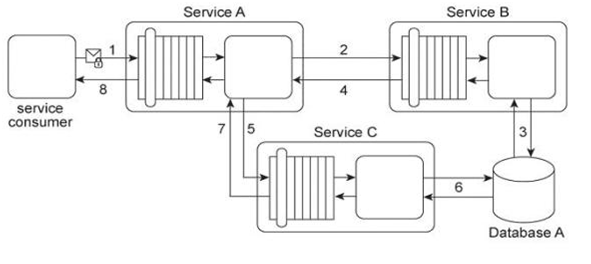
This service composition was recently shut down after it was discovered that Database A had been successfully attacked twice in a row. The first type of attack consisted of a series of coordinated request messages sent by the same malicious service consumer, with the intention of triggering a range of exception conditions within the database in order to generate various error messages. The second type of attack consisted of a service consumer sending request messages with malicious input with the intention of gaining control over the database server. This attack resulted in the deletion of database records and tables. An investigation revealed that both attacks were carried out by malicious service consumers that were authorized. How can the service composition security architecture be improved to prevent these types of attacks?
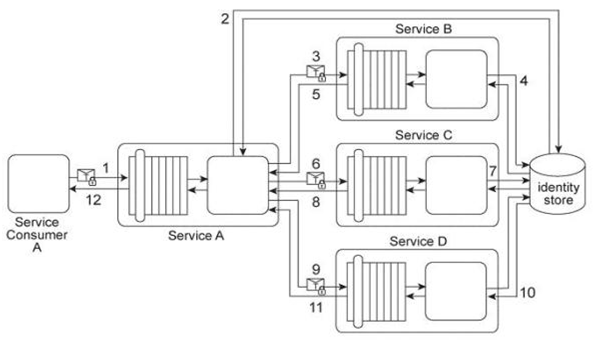
Service Consumer A sends a request message with a Username token to Service A (1). Service B authenticates the request by verifying the security credentials from the Username token with a shared identity store (2), To process Service Consumer A's request message. Service A must use Services B, C, and D .Each of these three services also requires the Username token (3. 6, 9) in order to authenticate Service Consumer A by using the same shared identity store (4, 7, 10). Upon each successful authentication, each of the three services (B, C, and D) issues a response message back to Service A (5, 8, 11). Upon receiving and processing the data in all three response messages, Service A sends its own response message to Service Consumer A (12). There are plans implement a single sign-on security mechanism in this service composition architecture. The service contracts for Services A, C, and D can be modified with minimal impact in order to provide support for the additional messaging requirements of the single sign-on mechanism. However, Service B's service contract is tightly coupled to its implementation and, as a result, this type of change to its service contract is not possible as it would require too many modifications to the underlying service implementation. Given the fact that Service B's service contract cannot be changed to support single sign-on, how can a single sign-on mechanism still be implemented across all services?
Service A provides a data access capability that can be used by a variety of service consumers. The database records accessed by Service A are classified as either private or public. There are two types of service consumers that use Service A:
Service consumers with public access permissions (allowed to access only public data records) and service consumers with private access permissions (allowed to access all data records). For performance reasons the Service A architecture uses a single database, named Database A .Each record in Database A is classified as either private or public. After Service A is invoked by a service consumer (1), it authenticates the request message using an identity store and retrieves the corresponding authorization (2, 3). Once authorized, the service consumer's request is submitted to Database A (4), which then returns the requested data (5) If the service consumer has private access permissions, all of the returned data is included in Service A's response message (6). If the service consumer has public access permissions, then Service A first filters the data in order to remove all unauthorized private data records, before sending to the response message to the service consumer (6). An investigation recently detected that private data has been leaked to unauthorized service consumers. An audit of the Service A architecture revealed that Service A's filtering logic is flawed, resulting in situations where private data was accidentally shared with service consumers that only have public access permissions. Further, it was discovered that attackers have been monitoring response messages sent by Service A in order to capture private data. It is subsequently decided to split Database A into two databases:
one containing only private data (the Private Database) and the other containing only public data (the Public Database). What additional changes are necessary to address these security problems?
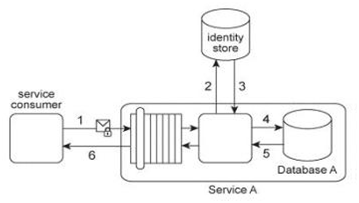
Service A has two specific service consumers, Service Consumer A and Service Consumer B (1). Both service consumers are required to provide security credentials in order for Service A to perform authentication using an identity store (2). If a service consumer's request message is successfully authenticated, Service A processes the request by exchanging messages with Service B (3) and then Service C (4). With each of these message exchanges, Service A collects data necessary to perform a query against historical data stored in a proprietary legacy system. Service A's request to the legacy system must be authenticated (5). The legacy system only provides access control using a single account. If the request from Service A is permitted, it will be able to access all of the data stored in the legacy system. If the request is not permitted, none of the data stored in the legacy system can be accessed. Upon successfully retrieving the requested data (6), Service A generates a response message that is sent back to either Service Consumer A or B .The legacy system is also used independently by Service D without requiring any authentication. Furthermore, the legacy system has no auditing feature and therefore cannot record when data access from Service A or Service D occurs. If the legacy system encounters an error when processing a request, it generates descriptive error codes. This service composition architecture needs to be upgraded in order to fulfill the following new security requirements:
1. Service Consumers A and B have different access permissions and therefore, data received from the legacy system must be filtered prior to issuing a response message to one of these two service consumers.
2. Service Consumer A's request messages must be digitally signed, whereas request messages from Service Consumer B do not need to be digitally signed. Which of the following statements describes a solution that fulfills these requirements?

Service Consumer A sends a request message to Service A (1), after which Service A sends a request message with security credentials to Service B (2). Service B authenticates the request and, if the authentication is successful, writes data from the request message into Database B (3). Service B then sends a request message to Service C (4), which is not required to issue a response message. Service B then sends a response message back to Service A (5). After processing Service B's response, Service A sends another request message with security credentials to Service B (6). After successfully authenticating this second request message from Service A, Service B sends a request message to Service D (7). Service D is also not required to issue a response message. Finally, Service B sends a response message to Service A (8), after which Service A records the response message contents in Database A (9) before sending its own response message to Service Consumer A (10). To use Service A, Service Consumer A is charged a per usage fee. The owner of Service Consumer A has filed a complaint with the owner of Service A, stating that the bills that have been issued are for more usage of Service A than Service Consumer A actually used. Additionally, it has been discovered that malicious intermediaries are intercepting and modifying messages being sent from Service B to Services C and D .Because Services C and D do not issue response messages, the resulting errors and problems were not reported back to Service B .Which of the following statements describes a solution that correctly addresses these problems?

Unlock All Questions for Arcitura Education S90.20 Exam
Full Exam Access, Actual Exam Questions, Validated Answers, Anytime Anywhere, No Download Limits, No Practice Limits
Get All 30 Questions & Answers