Most Recent Arcitura Education S90.20 Exam Questions & Answers
Prepare for the Arcitura Education SOA Security Lab exam with our extensive collection of questions and answers. These practice Q&A are updated according to the latest syllabus, providing you with the tools needed to review and test your knowledge.
QA4Exam focus on the latest syllabus and exam objectives, our practice Q&A are designed to help you identify key topics and solidify your understanding. By focusing on the core curriculum, These Questions & Answers helps you cover all the essential topics, ensuring you're well-prepared for every section of the exam. Each question comes with a detailed explanation, offering valuable insights and helping you to learn from your mistakes. Whether you're looking to assess your progress or dive deeper into complex topics, our updated Q&A will provide the support you need to confidently approach the Arcitura Education S90.20 exam and achieve success.
The questions for S90.20 were last updated on Dec 26, 2024.
- Viewing page 1 out of 6 pages.
- Viewing questions 1-5 out of 30 questions
Service A is a publically accessible service that provides free multimedia retrieval capabilities to a range of service consumers. To carry out this functionality, Service A is first invoked by Service Consumer A (1). Based on the nature of the request message received from Service Consumer A, Service A either invokes Service B or Service C .When Service B is invoked by Service A (2A) it retrieves data from publicly available sources (not shown) and responds with the requested data (3A). When Service C is invoked by Service A (2B) it retrieves data from proprietary sources within the IT enterprise (not shown) and responds with the requested data (3B). After receiving a response from Service B or Service C, Service A sends the retrieved data to Service Consumer A (4). Service B does not require service consumers to be authenticated, but Service C does require authentication of service consumers. The service contract for Service A therefore uses WS-Policy alternative policies in order to express the two different authentication requirements to Service Consumer A .When Service Consumer A sends a request message (1), Service A determines whether the request requires the involvement of Service C and then checks to ensure that the necessary security credentials were received as part of the message. If the credentials provided by Service Consumer A are verified. Service A creates a signed SAML assertion and sends it with the request message to Service C (2B) This authentication information is protected by public key encryption However, responses to Service Consumer A's request message (3B, 4) are not encrypted for performance reasons. The owner of Service C is planning two changes to the service architecture:
1. A fee will be charged to Service Consumer A (or any service consumer) using Service C .2. The response messages issued by Service C need to be secured in order to prevent unauthorized access. An analysis of Service C's usage statistics reveals that a group of service consumers specifically request the retrieval of multimedia data on a frequent basis. To promote the usage of Service C to these types of service consumers, the owner of Service C plans to offer a special discount by allowing unlimited multimedia retrievals for a fixed monthly price. Service consumers that do not subscribe to this promotion will need to pay for each request individually. It is anticipated that the new promotion will significantly increase the usage of Service C .The owner of Service C therefore wants to ensure that the security added to the response messages has a minimal impact on Service C's runtime performance. What steps can be taken to fulfill these requirements?

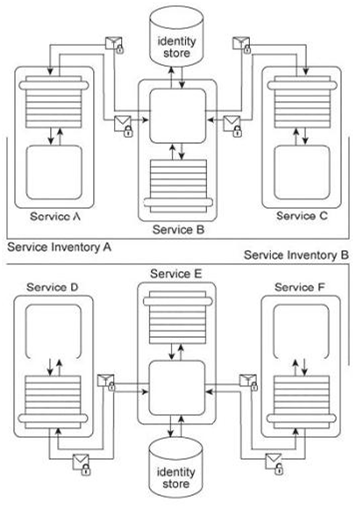
Services A, B, and C reside in Service Inventory A and Services D, E, and F reside in Service Inventory B .Service B is an authentication broker that issues WS-Trust based SAML tokens to Services A and C upon receiving security credentials from Services A and C .Service E is an authentication broker that issues WS-Trust based SAML tokens to Services D and F upon receiving security credentials from Services D and E .Service B uses the Service Inventory A identify store to validate the security credentials of Services A and C .Service E uses the Service Inventory B identity store to validate the security credentials of Services D and F .It is decided to use Service E as the sole authentication broker for all services in Service Inventories A and B .Service B is kept as a secondary authentication broker for load balancing purposes. Specifically, it is to be used for situations where authentication requests are expected to be extra time consuming in order to limit the performance burden on Service E .Even though Service B has all the necessary functionality to fulfill this new responsibility, only Service E can issue SAML tokens to other services. How can these architectures be modified to support these new requirements?
Service A is a publically accessible service that provides free multimedia retrieval capabilities to a range of service consumers. To carry out this functionality, Service A is first invoked by Service Consumer A (1). Based on the nature of the request message received from Service Consumer A, Service A either invokes Service B or Service C .When Service B is invoked by Service A (2A) it retrieves data from publicly available sources (not shown) and responds with the requested data (3A). When Service C is invoked by Service A (2B) it retrieves data from proprietary sources within the IT enterprise (not shown) and responds with the requested data (3B). After receiving a response from Service B or Service C, Service A sends the retrieved data to Service Consumer A (4). Service B does not require service consumers to be authenticated, but Service C does require authentication of service consumers. The service contract for Service A therefore uses WS-Policy alternative policies in order to express the two different authentication requirements to Service Consumer A .When Service Consumer A sends a request message (1), Service A determines whether the request requires the involvement of Service C and then checks to ensure that the necessary security credentials were received as part of the message. If the credentials provided by Service Consumer A are verified. Service A creates a signed SAML assertion and sends it with the request message to Service C (2B) This authentication information is protected by public key encryption However, responses to Service Consumer A's request message (3B, 4) are not encrypted for performance reasons. Recently, the usage of Service C has noticeably declined. An investigation has revealed response messages issued by Service C (3B) have been repeatedly intercepted and accessed by unauthorized and malicious intermediaries. As a result, Service Consumer A has lost confidence in the use of Service A for the retrieval of proprietary data because it is being viewed as a security risk. This is especially troubling, because the owner of Service A had planned to start charging a fee for Service A's ability to provide proprietary data via the use of Service C .How can this service composition architecture be changed to address the security problem with minimal impact on runtime performance?

Service A provides a data access capability that can be used by a variety of service consumers. The database records accessed by Service A are classified as either private or public. There are two types of service consumers that use Service A:
Service consumers with public access permissions (allowed to access only public data records) and service consumers with private access permissions (allowed to access all data records). For performance reasons the Service A architecture uses a single database, named Database A .Each record in Database A is classified as either private or public. After Service A is invoked by a service consumer (1), it authenticates the request message using an identity store and retrieves the corresponding authorization (2, 3). Once authorized, the service consumer's request is submitted to Database A (4), which then returns the requested data (5) If the service consumer has private access permissions, all of the returned data is included in Service A's response message (6). If the service consumer has public access permissions, then Service A first filters the data in order to remove all unauthorized private data records, before sending to the response message to the service consumer (6). An investigation recently detected that private data has been leaked to unauthorized service consumers. An audit of the Service A architecture revealed that Service A's filtering logic is flawed, resulting in situations where private data was accidentally shared with service consumers that only have public access permissions. Further, it was discovered that attackers have been monitoring response messages sent by Service A in order to capture private data. It is subsequently decided to split Database A into two databases:
one containing only private data (the Private Database) and the other containing only public data (the Public Database). What additional changes are necessary to address these security problems?
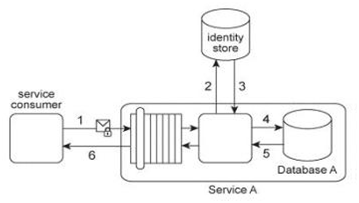
Service Consumer A submits a request message with security credentials to Service A (1). The identity store that Service A needs to use in order to authenticate the security credentials can only be accessed via a legacy system that resides in a different service inventory. Therefore, to authenticate Service Consumer A, Service A must first forward the security credentials to the legacy system (2). The legacy system then returns the requested identity to Service A (3). Service A authenticates Service Consumer A against the identity received from the legacy system. If the authentication is successful, Service A retrieves the requested data from Database A (4), and returns the data in a response message sent back to Service Consumer A (5). Service A belongs to Service Inventory A which further belongs to Security Domain A and the legacy system belongs to Service Inventory B which further belongs to Security Domain B .(The legacy system is encapsulated by other services within Service Inventory B, which are not shown in the diagram.) These two security domains trust each other. Communication between Service A and the legacy system is kept confidential using transport-layer security. It was recently discovered that a malicious attacker, posing as Service Consumer A, has been accessing Service A .An investigation revealed that these attacks occurred because security credentials supplied by Service Consumer A were transmitted in plaintext. Furthermore, vulnerabilities to replay attacks and malicious intermediaries have been detected. Which of the following statements describes a solution that can counter these types of attacks?
Also, list the industry standards required by the proposed solution.

Unlock All Questions for Arcitura Education S90.20 Exam
Full Exam Access, Actual Exam Questions, Validated Answers, Anytime Anywhere, No Download Limits, No Practice Limits
Get All 30 Questions & Answers