Most Recent Dell EMC D-SF-A-24 Exam Questions & Answers
Prepare for the Dell EMC Dell Security Foundations Achievement exam with our extensive collection of questions and answers. These practice Q&A are updated according to the latest syllabus, providing you with the tools needed to review and test your knowledge.
QA4Exam focus on the latest syllabus and exam objectives, our practice Q&A are designed to help you identify key topics and solidify your understanding. By focusing on the core curriculum, These Questions & Answers helps you cover all the essential topics, ensuring you're well-prepared for every section of the exam. Each question comes with a detailed explanation, offering valuable insights and helping you to learn from your mistakes. Whether you're looking to assess your progress or dive deeper into complex topics, our updated Q&A will provide the support you need to confidently approach the Dell EMC D-SF-A-24 exam and achieve success.
The questions for D-SF-A-24 were last updated on Dec 23, 2024.
- Viewing page 1 out of 4 pages.
- Viewing questions 1-5 out of 20 questions
During the analysis, the threat intelligence team disclosed that attackers not only encrypted files, but also attempted to encrypt backups and shared, networked, and cloud drives.
Which type of ransomware is used for this attack?
A .R.T.I.E. is planning to deploy some of their applications in a public cloud. A major concern is how to share and protect data off premises. Also, how data can be used in decision making without exposing it to anyone who should not have access. Dell Services briefed them about various control mechanisms to secure data in the public cloud.
Which control mechanism should be selected in this scenario?
Control Mechanism Selection:
For A .R.T.I.E.'s scenario, where the concern is about sharing and protecting data off-premises and ensuring that data can be used in decision-making without exposing it to unauthorized access, the most suitable control mechanism would be:
A . Proactive control mechanism
A .R.T.I.E. has an evolving need, which was amplified during the incidents. Their complex and dispersed IT environments have thousands of users, applications, and resources to manage. Dell found that the existing Identity and Access Management was limited in its ability to apply expanding IAM protection to applications beyond the core financial and human resource management application. A .R.T.I.E. also did not have many options for protecting their access especially in the cloud. A .R.T.I.E. were also not comfortable exposing their applications for remote access.
Dell recommended adopting robust IAM techniques like mapping out connections between privileged users and admin accounts, and the use multifactor authentication.
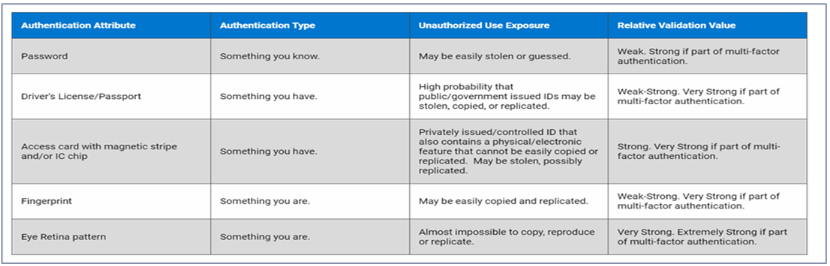
The Dell Services team suggest implementing a system that requires individuals to provide a PIN and biometric information to access their device.
Which type of multifactor authentication should be suggested?
The recommended multifactor authentication (MFA) type for A .R.T.I.E., as suggested by Dell Services, is A. Something you have and something you are. This type of MFA requires two distinct forms of identification: one that the user possesses (something you have) and one that is inherent to the user (something you are).
Something you have could be a physical token, a security key, or a mobile device that generates time-based one-time passwords (TOTPs).
Something you are refers to biometric identifiers, such as fingerprints, facial recognition, or iris scans, which are unique to each individual.
By combining these two factors, the authentication process becomes significantly more secure than using any single factor alone. The physical token or device provides proof of possession, which is difficult for an attacker to replicate, especially without physical access. The biometric identifier ensures that even if the physical token is stolen, it cannot be used without the matching biometric input.
The use of MFA is supported by security best practices and standards, including those outlined by the National Institute of Standards and Technology (NIST).
Dell's own security framework likely aligns with these standards, advocating for robust authentication mechanisms to protect against unauthorized access, especially in cloud environments where the attack surface is broader.
In the context of A .R.T.I.E.'s case, where employees access sensitive applications and data remotely, implementing MFA with these two factors will help mitigate the risk of unauthorized access and potential data breaches. It is a proactive step towards enhancing the organization's security posture in line with Dell's strategic advice.
The security team recommends the use of User Entity and Behavior Analytics (UEBA) in order to monitor and detect unusual traffic patterns, unauthorized data access, and malicious activity of A .R.T.I.E. The monitored entities include A .R.T.I.E. processes, applications, and network devices Besides the use of UEBA, the security team suggests a customized and thorough implementation plan for the organization.
What are the key attributes that define UEBA?
The cybersecurity team must create a resilient security plan to address threats. To accomplish this, the threat intelligence team performed a thorough analysis of the A .R.T.I.E. threat landscape. The result was a list of vulnerabilities such as social engineering, zero-day exploits, ransomware, phishing emails, outsourced infrastructure, and insider threats.
Using the information in the case study and the scenario for this question, which vulnerability type exposes the data and infrastructure of A.R.T.I.E .?
Unlock All Questions for Dell EMC D-SF-A-24 Exam
Full Exam Access, Actual Exam Questions, Validated Answers, Anytime Anywhere, No Download Limits, No Practice Limits
Get All 20 Questions & Answers