Most Recent Fortinet NSE7_ADA-6.3 Exam Questions & Answers
Prepare for the Fortinet NSE 7 - Advanced Analytics 6.3 exam with our extensive collection of questions and answers. These practice Q&A are updated according to the latest syllabus, providing you with the tools needed to review and test your knowledge.
QA4Exam focus on the latest syllabus and exam objectives, our practice Q&A are designed to help you identify key topics and solidify your understanding. By focusing on the core curriculum, These Questions & Answers helps you cover all the essential topics, ensuring you're well-prepared for every section of the exam. Each question comes with a detailed explanation, offering valuable insights and helping you to learn from your mistakes. Whether you're looking to assess your progress or dive deeper into complex topics, our updated Q&A will provide the support you need to confidently approach the Fortinet NSE7_ADA-6.3 exam and achieve success.
The questions for NSE7_ADA-6.3 were last updated on Jan 20, 2025.
- Viewing page 1 out of 7 pages.
- Viewing questions 1-5 out of 34 questions
Refer to the exhibit.

Which statement about the rule filters events shown in the exhibit is true?
The rule filters events with an event type that belong to the Domain Account Locked CMDB group and a reporting IP that belong to the Domain Controller applications group. This means that only events that have both criteria met will be processed by this rule. The event type and reporting IP are joined by an AND operator, which requires both conditions to be true.
Which statement about EPS bursting is true?
FortiSIEM allows EPS bursting to handle event spikes without dropping events or violating the license agreement. EPS bursting means that FortiSIEM will let you burst up to five times the licensed EPS at any given time, provided it has accumulated enough unused EPS from previous time intervals.
Refer to the exhibit.

An administrator wants to remediate the incident from FortiSIEM shown in the exhibit.
What option is available to the administrator?
The incident from FortiSIEM shown in the exhibit is a brute force attack on a FortiGate device. The remediation option available to the administrator is to run the block IP FortiOS 5.4 action, which will block the source IP address of the attacker on the FortiGate device using a firewall policy.
Refer to the exhibit.
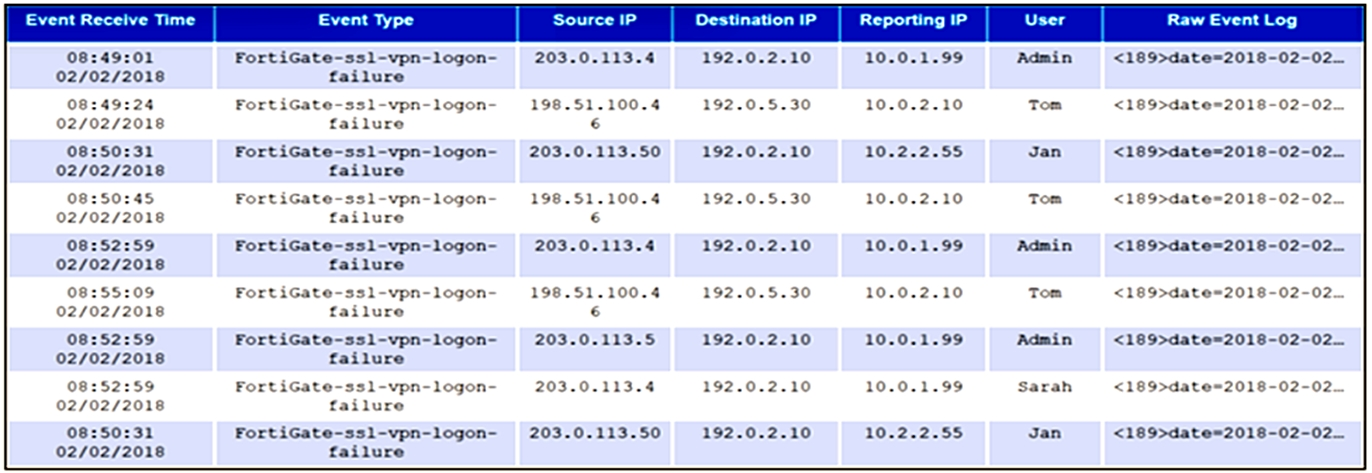
An administrator runs an analytic search for all FortiGate SSL VPN logon failures. The results are grouped by source IP, reporting IP, and user. The administrator wants to restrict the results to only those rows where the COUNT >= 3.
Which user would meet that condition?
The user who would meet that condition is Tom. Tom has four rows in the results where the COUNT is greater than or equal to three, meaning he had at least three SSL VPN logon failures from the same source IP and reporting IP. The other users have either less than three rows or less than three COUNT in each row.
Unlock All Questions for Fortinet NSE7_ADA-6.3 Exam
Full Exam Access, Actual Exam Questions, Validated Answers, Anytime Anywhere, No Download Limits, No Practice Limits
Get All 34 Questions & Answers